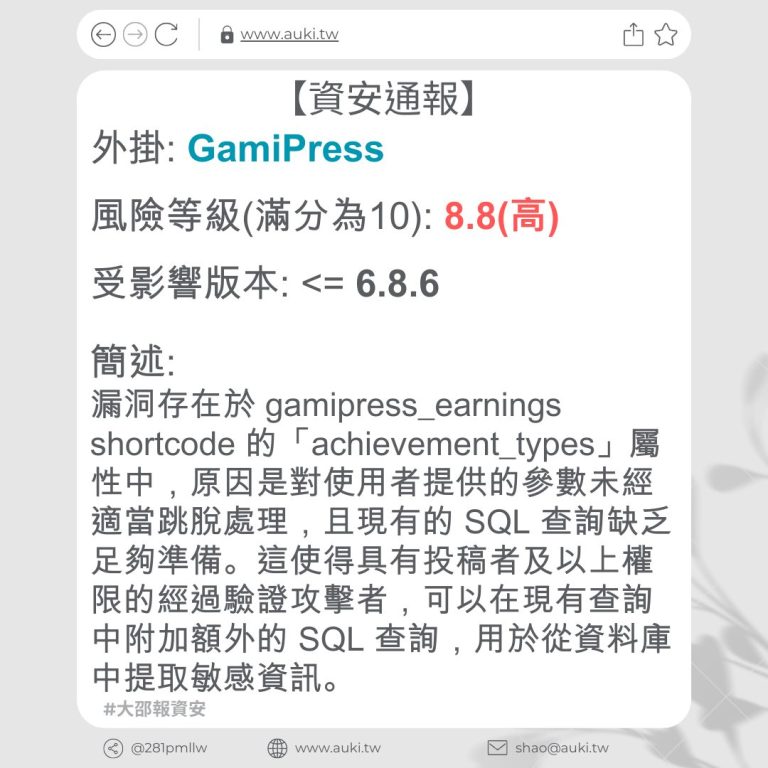
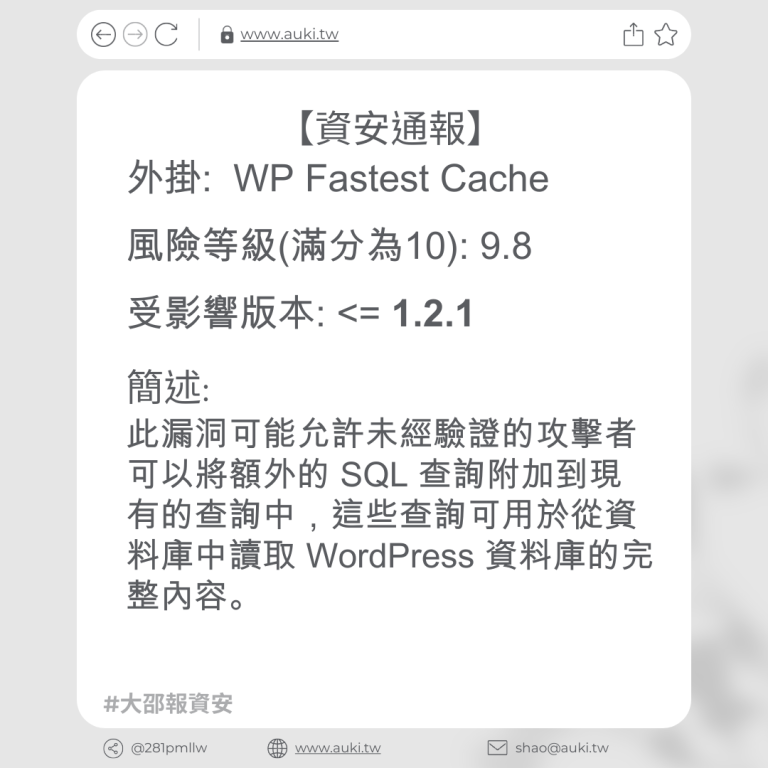
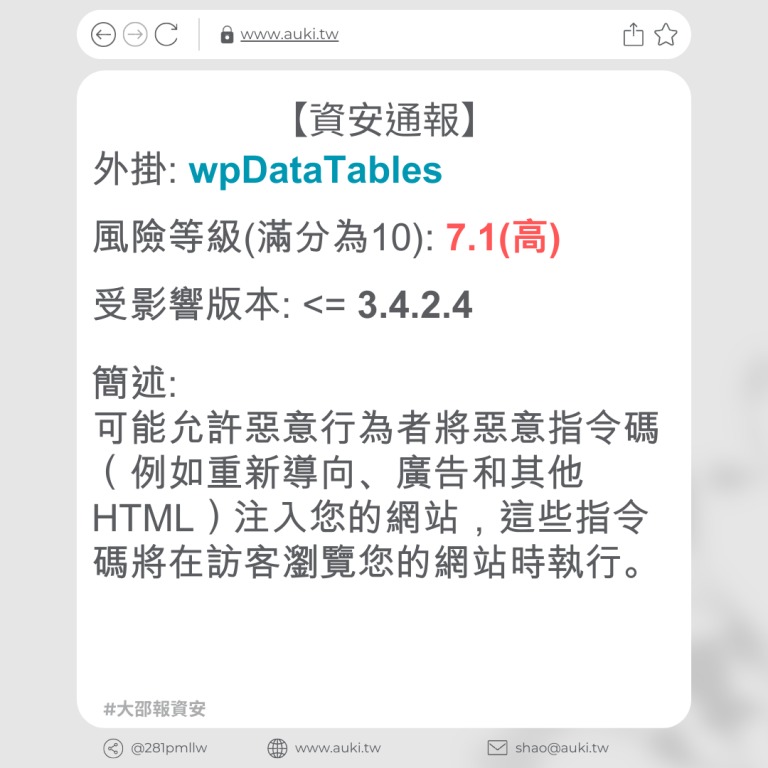
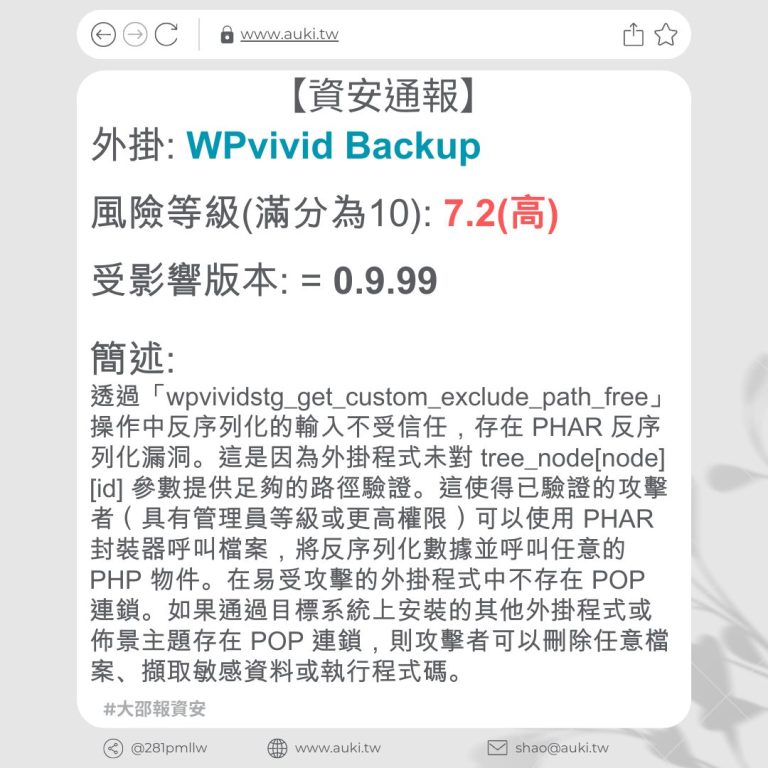
【資安通報】
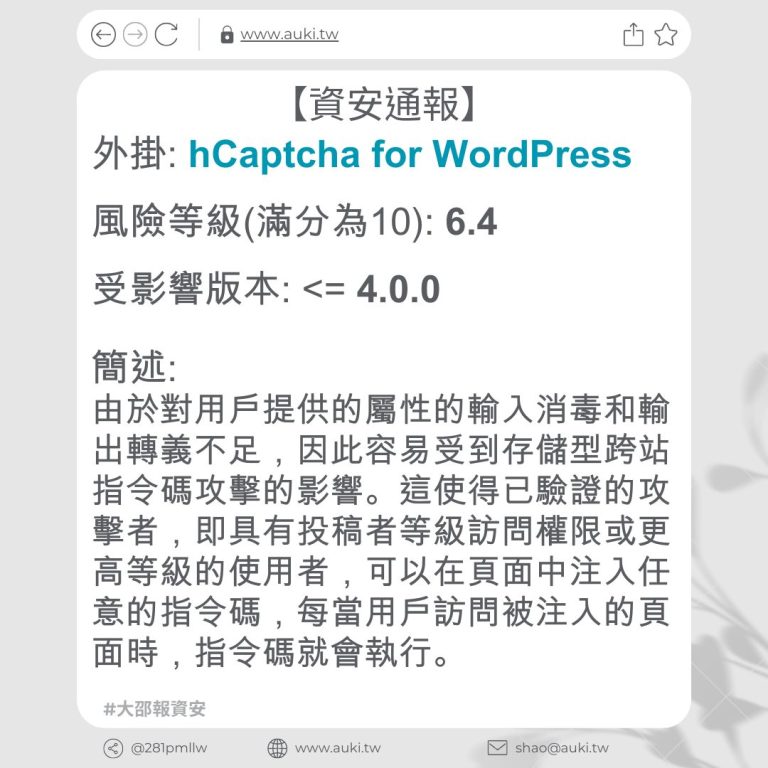
風險等級(滿分為10分): 6.4
受影響版本: <= 5.6.3
簡述:
該漏洞是通過文件夾名稱參數進行存儲型跨站指令碼攻擊,原因是未進行足夠的輸入清理和輸出轉義。這使得已驗證的攻擊者,只要擁有作者訪問權限或更高權限,就可以在頁面中注入任意指令碼,並在訪客瀏覽注入頁面時執行該指令碼。
參考資料:
- https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/filebird/filebird-wordpress-media-library-folders-file-manager-563-authenticated-author-stored-cross-site-scripting
- https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/filebird/filebird-wordpress-media-library-folders-file-manager-563-authenticated-author-insecure-direct-object-reference
#大邵報資安
#WordPress