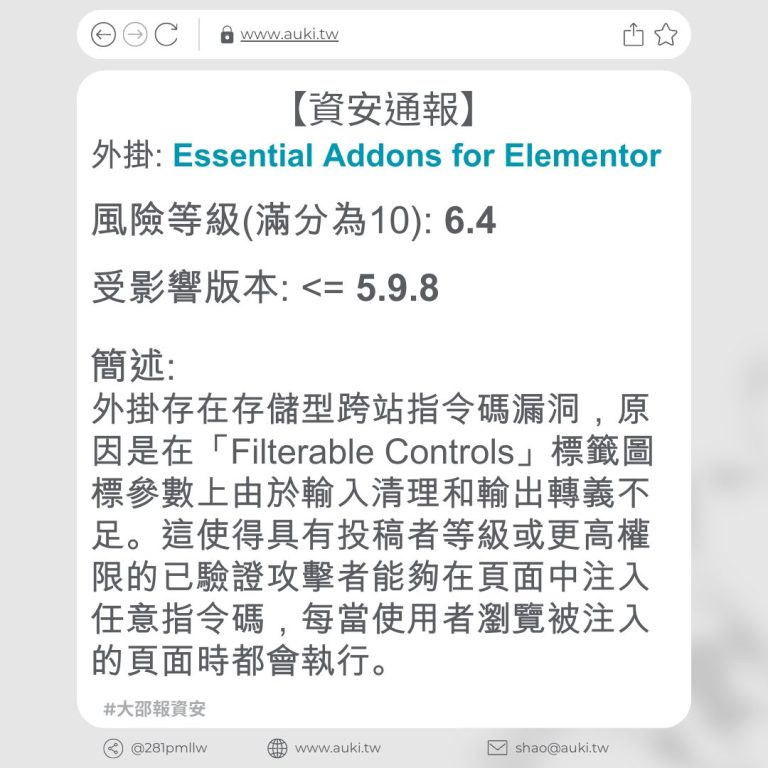
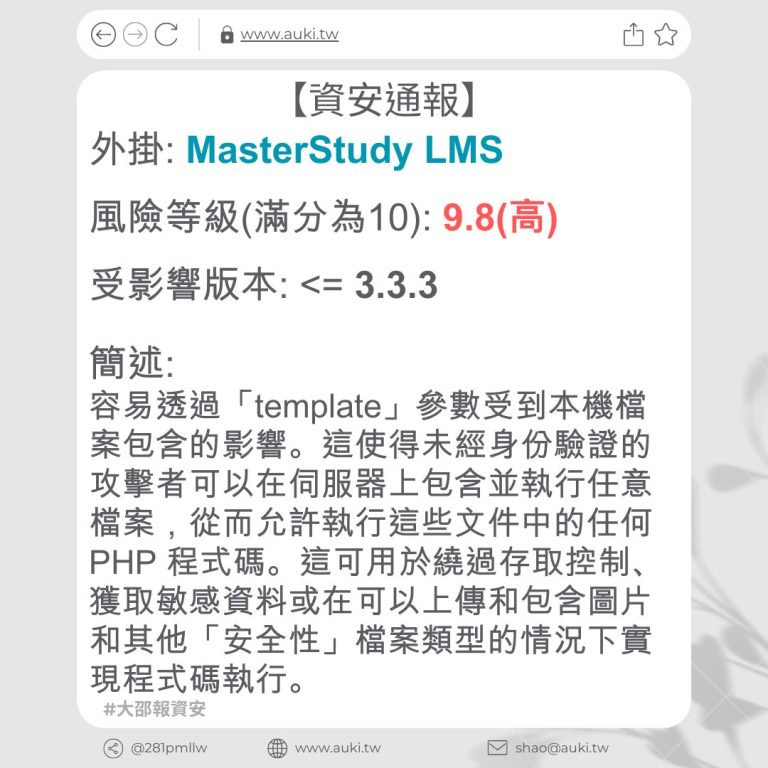
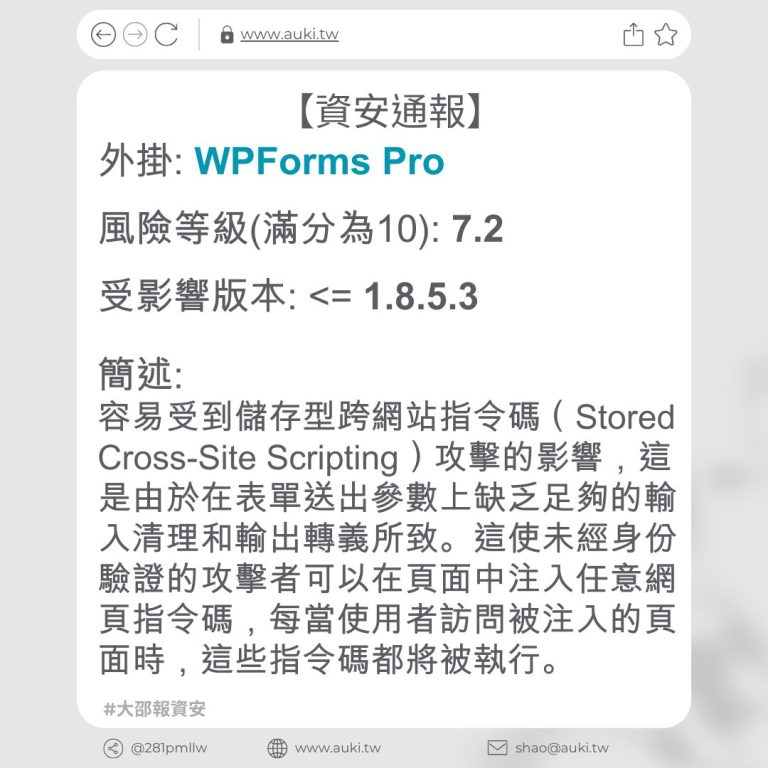
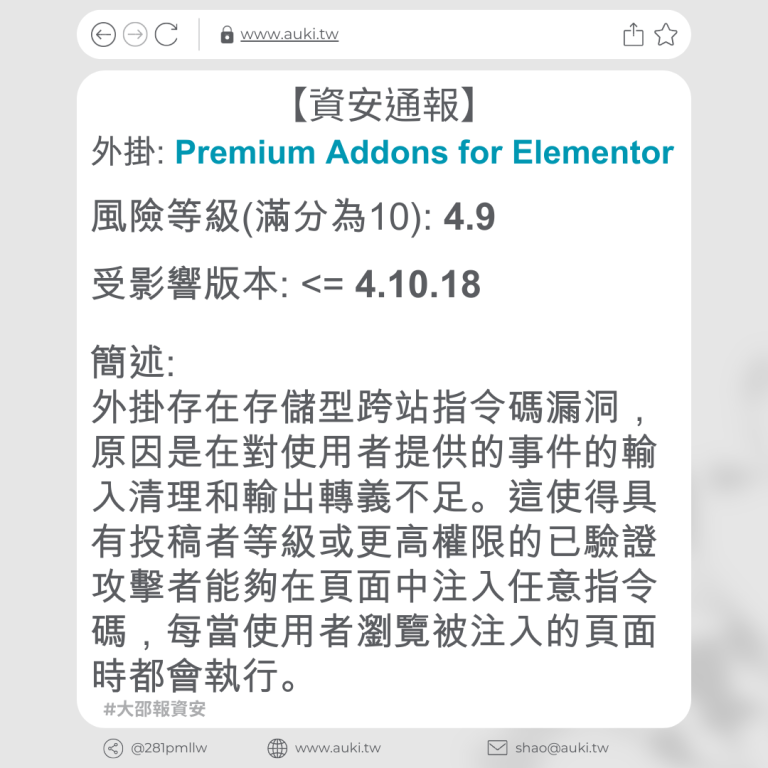
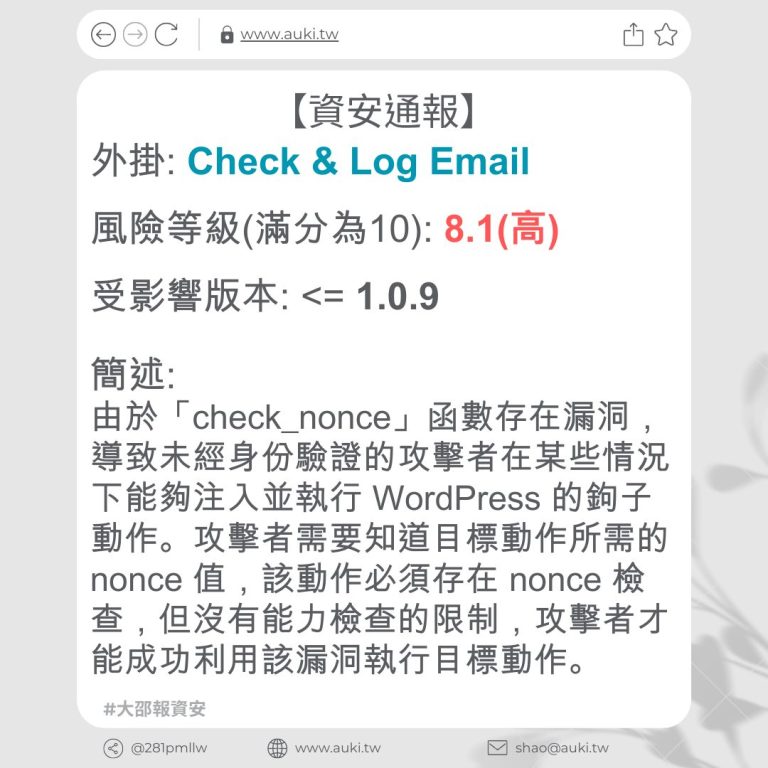
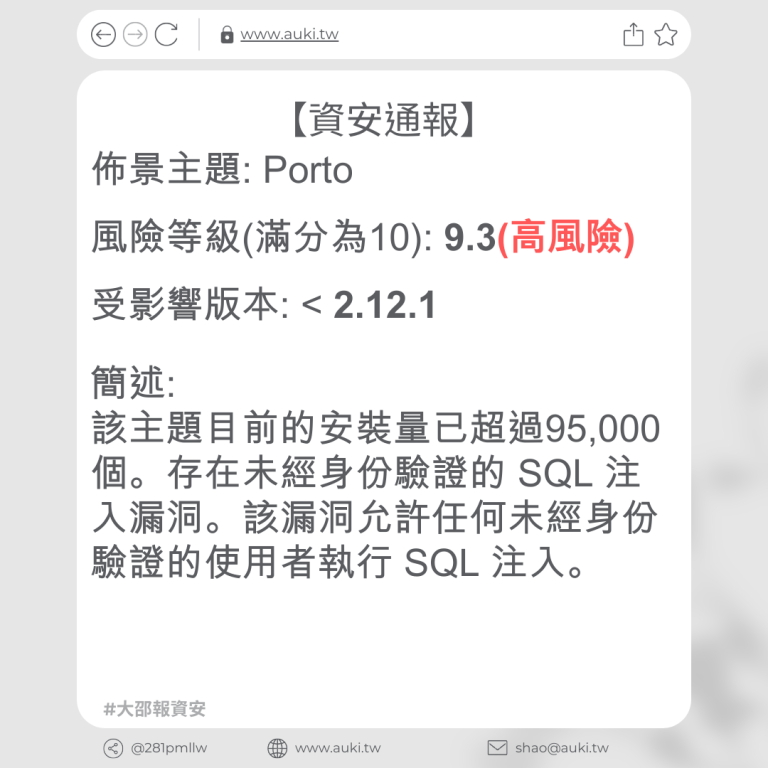
【資安通報】
風險等級(滿分為10分): 6.4
受影響版本: <= 3.20.1
簡述:
由於「video_html_tag」屬性、小工具的「custom_id」「Media Carousel」屬性以及表單小工具上傳 SVGZ 輸入未經適當清理及輸出未正確轉義,存在儲存型跨站指令碼漏洞。具有投稿者及以上權限的經過驗證的攻擊者,可在頁面中注入任意網頁指令碼,當使用者瀏覽被注入的頁面時,惡意指令碼將會執行。
注意:表單小工具上傳 SVGZ 漏洞只會在執行 NGINX 的 Web 伺服器上利用。它無法在執行 Apache HTTP Server 的 Web 伺服器上被利用。
參考資料:
- https://patchstack.com/database/vulnerability/elementor-pro/wordpress-elementor-pro-plugin-3-20-1-auth-stored-cross-site-scripting-xss-vulnerability-3
- https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/elementor-pro/elementor-website-builder-pro-3201-authenticated-contributor-stored-cross-site-scripting-via-form-widget-svgz-file-upload
- https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/elementor-pro/elementor-website-builder-pro-3201-authenticated-contributor-stored-cross-site-scripting
- https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/elementor-pro/elementor-website-builder-pro-3201-authententicated-contributor-stored-cross-site-scripting
- https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/elementor-pro/elementor-website-builder-pro-3201-authenticated-contributor-dom-based-stored-cross-site-scripting-via-video-html-tag
#大邵報資安
#WordPress